By Ameet Dhillon, Director of Business Development, Accolade Technology
BTC
We are all familiar with the term “industry-standard” or “commercial off-the-shelf (COTS)” servers. The generally accepted understanding is these are servers which contain readily available components such as an x86 CPU, memory, storage, networking and a ubiquitous operating system such as Linux or Windows.
We usually think of companies like Dell or HP as suppliers of these industry-standard servers, and over time have come to accept that the best platform for our datacenter applications is an industry-standard server. This is certainly true for a large percentage of applications, but we shouldn’t automatically assume there are no other options.
A slight twist to the industry-standard server, which still includes all the standard components, would be the addition of an onboard FPGA. I don’t mean an FPGA as a “bolt-on” in the form of a PCIe adapter/NIC (though that is a valid solution as well), but rather an FPGA that is mounted onto the motherboard and wired up to interact with the various components around it. Just like all the other components, the FPGA performs a specific and vital function; namely host CPU offload.
An FPGA is a programmable device well-suited to performing application specific functions or algorithms. These functions run the gamut from something very specific such as a proprietary security algorithm to more generic requirements such as time stamping, packet filtering or data deduplication.
A repetitive and CPU intensive task is the ideal candidate for offload to an FPGA. It is not uncommon to reduce CPU load by over 50 percent with the help of an FPGA. In addition, FPGA offload enables remarkable scaling of data center applications previously restricted by CPU bottlenecks.
While the benefits of an onboard or “native” FPGA can be very compelling, there are at least two potential downsides to keep in mind. The first is simply cost. Integrating an FPGA can add a relatively significant cost to the server.
However, the return on investment (ROI) is usually quite apparent if your data center application performs repetitive tasks which can be offloaded. Since FPGA offload dramatically reduces the burden on your host CPUs, thereby optimizing application performance, these added benefits are often well worth the cost.
The second downside is FPGA programming complexity. In the FPGA world, you don’t call someone a programmer but rather a “designer” or “design engineer.” This is because FPGAs are not programmed in common languages such as C or Java.
Rather, FPGAs are designed using Verilog or VHDL which are hardware description languages (HDLs) used to model electronic systems. For this reason, it is often not possible for a software application development team to program an FPGA with the specific offload function or algorithm they need to achieve the desired level of CPU offload.
The solution to this dilemma is to partner with a vendor that has expertise in FPGA design and can provide comprehensive offload functions as well as custom features tailored for each specific customer scenario.
Accolade Technology is a vendor that fits such a profile with its ATLAS-1000 FPGA integrated platform.
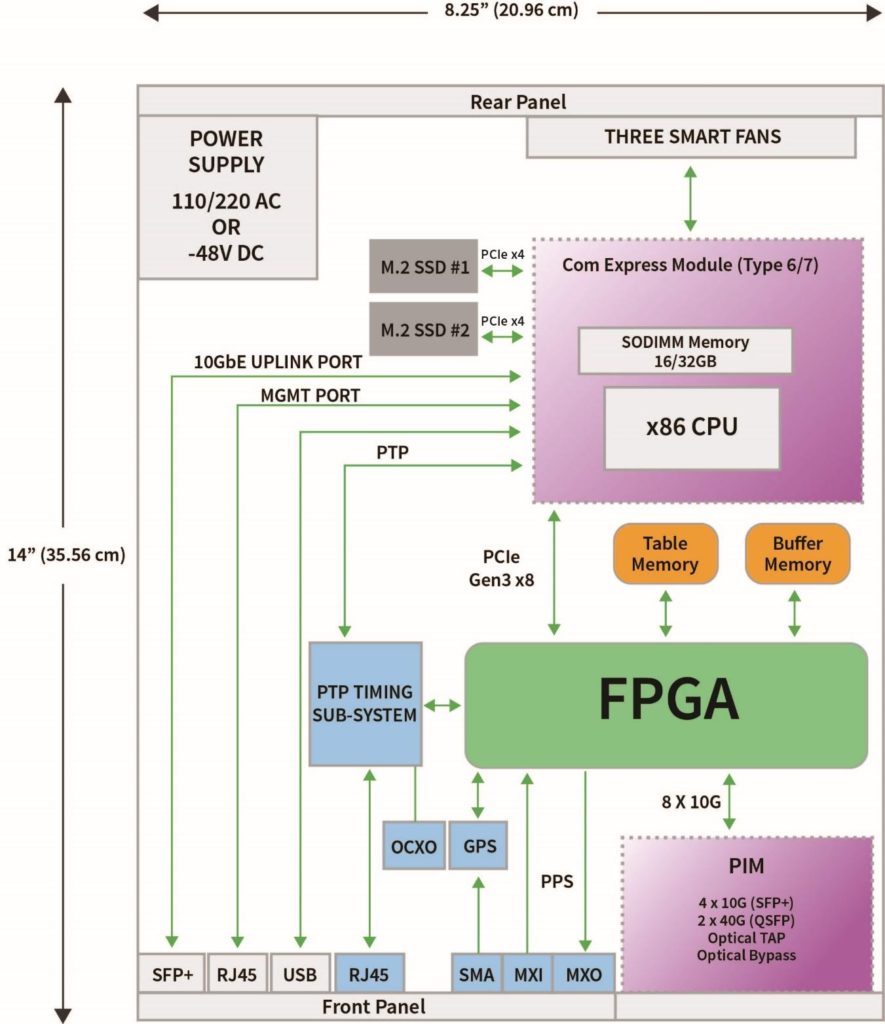
Figure 1 shows the 1U, half-width, ATLAS-1000 incorporating a Xilinx FPGA natively on the motherboard.
Like industry-standard servers, the ATLAS-1000 provides a multi-core Intel CPU, memory and storage along with an FPGA loaded with packet processing capabilities such as lossless packet capture, packet filtering, nanosecond precision timestamping, deduplication, flow classification and multi-core DMA.
In addition to the onboard FPGA, the platform has several other unique attributes such as direct GPS decode on the motherboard, pluggable interface modules that support 10 or 40G and a small footprint that accommodates two ATLAS-1000 units mounted side-by-side in a standard 19-inch rack.
Figure 2 shows a comprehensive architectural layout of this hardened platform. The platform is ideal for network/cyber security or monitoring applications such as DPI, NetFlow exporting, data deduplication or cluster load balancing.
For Website Source of details visit
this link.